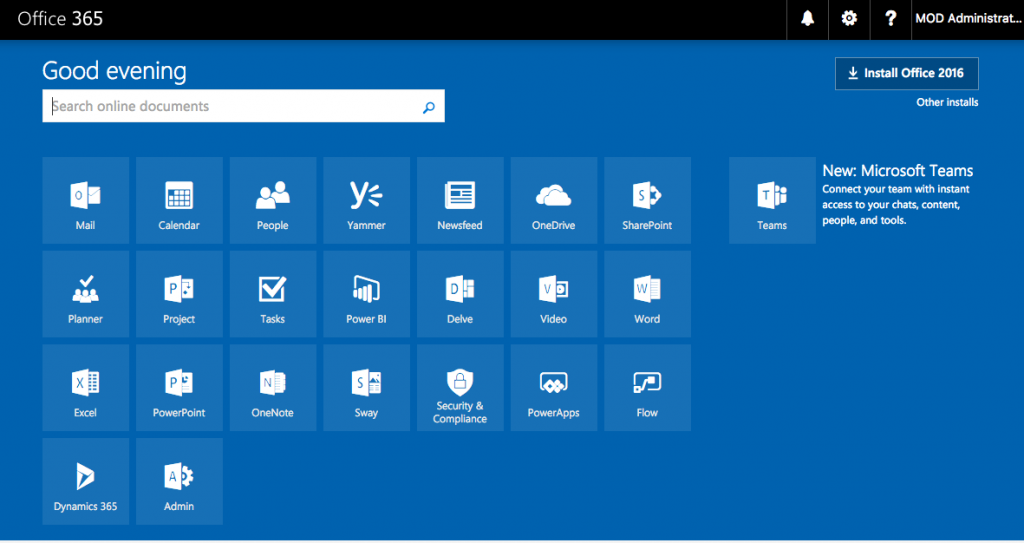
What is Microsoft Office 365 for Businesses.
Office 365 is a subscription based version of the popular Microsoft Office Software and other productivity tools. It has the added benefit of being cloud based and can be accessed via an internet browser.
Office 365 has a variety of subscription plans from as little as $2/user/month to $35/user/month. The plans are designed to cater to different business productivity needs and different sizes.
Most of the Office 365 plans provide a desktop and cloud based version of the Office applications. The Office applications can be installed on up to five devices (Desktop, Laptops & Phones) per each subscribed user, this makes it possible for users to work from a variety of devices.
Some of the applications included in Office 365 are:
- Microsoft Word
- Microsoft Excel
- Microsoft Access
- Microsoft PowerPoint
- Microsoft Outlook
- Exchange Online
- SharePoint Online
- Microsoft Teams
- Microsoft Groups
- Microsoft Yammer
- Microsoft Delve
- Power BI
How to Purchase Office 365
Office 365 can be purchased directly from Microsoft website or from a Microsoft Partner. We are a Microsoft Partner and assist businesses in selecting, purchase, installation and support of all Office 365 plans.
How to Access and Download Office 365
You can login to Office by going to the Office 365 Portal. Once you are in you can download Office 365 software like Word, Excel, Outlook and PowerPoint. You can also access the online version of all the available software.
Some Benefits of Office 365 for Businesses:
- Pay-AS-You-Go: Office 365 is a software as a service (SAAS), this means you pay for it like an utility bill. This frees up cash for other business expense. You can pay on a monthly or yearly basis. Paying yearly is a cheaper than monthly.
- Up-to-date Softwares: Office 365 is delivered via the cloud so you will have always have the latest features and most up-to-date versions. This is one less IT support service to pay for.
- Access Data from Anywhere: You have the option of storing your data in cloud via Office 365 and accessing from anywhere via an internet browser. This provides the ability for employees to work from anywhere
- Advanced Data Security: Microsoft has better data security than any small business could ever implement. Data is stored in secure data centers and encrypted in transit.
- No Servers to Maintain: You do not need a server to host Microsoft Office, SharePoint or even a file server for data storage. This also saves on server maintenance and electricity cost.
Office 365 Plans
There are different Office 365 plans to suit almost all business needs. Some plans and the scenarios for usage are:
Exchange Online for hosted Business Class Email.
SharePoint Online for Online file storage, Internal Team Site and Project Collaboration.
Kiosk Plans for communication and email access for Desk-less and Shift Workers.
Office 365 Business Premium for Small Business that need online and desktop versions of Office products.
Office 365 Enterprise E3 for businesses that need data security and compliance requirements.
Office 365 Enterprise E5 for businesses that need advanced data security, regulatory compliance, seamless communication in and out of the office.
Contact Us If you are thinking of moving to Office 365 or would like a free Demo to find out how it can benefit your business.